Welcome dear Networkseclearners to this new tutorial which is the Part 2 of Threat Analysis and Risk Assessment! I hope you liked part 1 and are looking forward to this part 2. If you haven’t read Automotive Cybersecurity Threat Analysis and Risk Assessment Part 1 yet, I strongly recommend you to read it before continuing. 🤲
As a reminder, in Part 1, we explored the most important concepts about the Threat Analysis and Risk Assessment (TARA) as outlined in the ISO/SAE 21434 standard. We covered the process essential steps involved in identifying and analyzing potential threats to automotive electronic systems and of course in assessing the associated risks.
Now, in Part 2, we’ll transition from theory to practice to provide you with a concrete example of how the TARA process is applied to a real world automotive system. I didn’t want to reuse the HeadLamp System example from the standard and preferred to choose an automtotive electronic system whose functionality speaks to everybody, is very easy to understand and which is critical so that we can easily understand the impact of cybersecurity on it. So, I selected the System called Brake By Wire since braking is common to everybody and is a critical feature of vehicles. Indeed, the Brake By Wire system is an innovative system that replaces traditional hydraulic braking with electronic control and offers enhanced performance and safety but also presents new cybersecurity challenges.
In this tutorial, we will walk through each step of the TARA process, demonstrating how to identify potential threats, assess their impact, and determine the appropriate risk mitigation strategies. But before, I will try to explain the concepts of Brake By Wire system to you.
By the end of this tutorial, you will have a better understanding on how to apply TARA in practice to protect automotive systems from cybersecurity threats, ensuring both safety and compliance with industry standards.
So, let’s get started! 😊
1. what is it Brake By Wire (BBW) System ? 🤔🤔
I am sure you have been looking forward to know what is this brake system we are talking about. Now, it is high time I told what it is. Indeed, Brake by Wire (BBW) System is an advanced braking system in modern cars that uses electronic signals instead of traditional mechanical or hydraulic links to control the brakes. With the BBW, the brakes are now controlled by electronics unlike the traditional hydraulic or mechanical control. In order to illustrate how this system works and the components it is composed of, I made an extremely simplified schematic. I want to insist in the fact that this schematic is extemely simplified and some details were abstracted in order to keep it simple and easy to understand. The main purpose of this schematic is to help you understand how the system operates. if you need to know all the details, I recommend you check these internet ressources :
Are you ready now for my schematic? Ding, ding, here it is 😉😉:
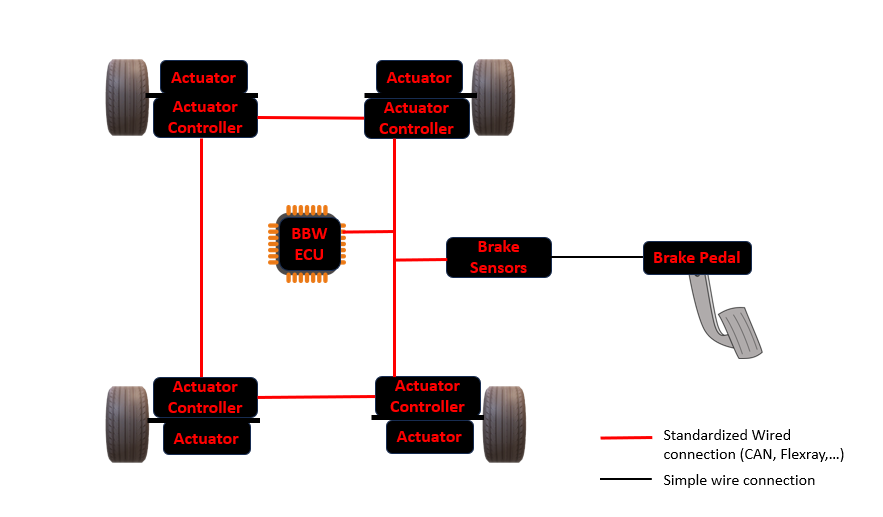
Now, I propose that we walk through all the components and describe them. Let’s start with what we are all familiar which is the Brake Pedal. I hope so :
- Brake Pedal : This is the pedal you press with your foot when you want to slow down or stop the vehicle. In a BBW system, pressing the brake pedal doesn’t directly activate the brakes mechanically. Instead, it will initiate an electronic process.
- Brake Sensors : These sensors are responsible for detecting how much pressure you’re applying to the brake pedal. They measure the force at which you press the pedal. This physical information is converted into electrical signal which is then sent to the Brake By Wire Electronic Control Unit (BBW ECU).
- BBW ECU (Brake By Wire Electronic Control Unit) : This is the central computer and also the brain of the entire system that manages the entire braking process. It receives data from the brake sensors and calculates the exact amount of braking force required at each wheel. After its processing, the ECU sends electronic commands to the actuators controlers telling them how much much to brake. The BBW ECU incorporates redundancy and fault tolerance to ensure safety and reliability.
- Actuator Controllers : These controllers act as the middlemen between the BBW ECU and the actuators. Each wheel has its own controller which takes the instructions from the BBW ECU and tells the actuators how much braking force to apply. This ensures that each wheel brakes properly.
- Actuators : These are the devices that physically apply the brakes to the wheels. Instead of using hydraulic fluid like traditional systems, the actuators in a BBW system operate electronically. They receive signals from the actuator controllers and apply the necessary braking force to slow down or stop the vehicle.
2. Application of TARA on The Brake By Wire System
I know you have been waiting for this part. We will not lose time anymore and will jump into the topic. I would like to recommend you to check again Automotive Cybersecurity Threat Analysis and Risk Assessment Part 1 if you need any information about all steps of the TARA process. Let’s get started with the item definition. 😊
2.1 Item Definition
In this section, in order to illustrate the item boundary and the preliminary architecture, I created a simplified context diagram of the Brake By Wire system. Some details were abstracted for the seek of simplicity. Take it again as a way to manage the complexity in a simple manner. Also, I would like to remind you that I am not an expert of Brake By Wire. If you are an expert of BBW reading this article, please, don’t hesitate to comment to correct eventually some mistakes or propose some improvements.
Here it is 😉 :
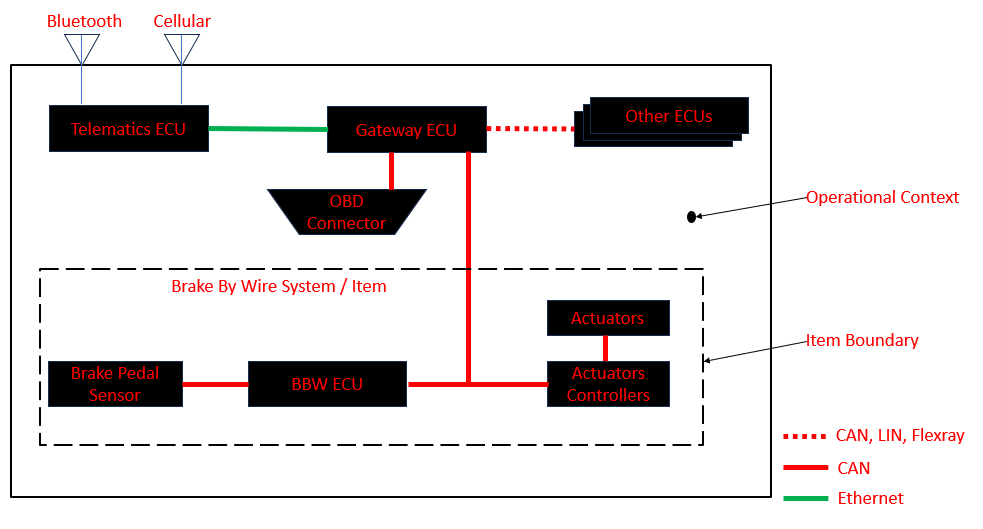
The Brake-by-Wire (BBW) system controls the braking of the vehicle based on driver input through the brake pedal. When the driver presses the brake pedal, the BBW system processes this input electronically and determines the appropriate amount of braking force to be applied to each wheel. The system is capable of adjusting the braking force in real-time to maintain vehicle stability and optimize stopping performance. Additionally, the BBW system can integrate with advanced safety features such as Anti-lock Braking System (ABS) and Electronic Stability Control (ESC) to prevent wheel lockup and maintain vehicle control during emergency braking.
The functionality of the Brake-by-Wire system does not depend on the Telematics ECU, Gateway ECU, or other vehicle systems for its core braking functions. However, it does interface with these systems to receive and send information, particularly for diagnostics, vehicle network communication, and certain safety features.
The item (Brake-by-Wire system) is connected with the gateway ECU, and the gateway ECU is connected with the telematics ECU by data communication. The Telematics ECU has external communication interfaces which Bluetooth and Cellular. This allows the vehicle to communicate with the external world.
Gateway ECU has external communication interfaces which are OBD connector and CAN, LIN, and FlexRay bus connections.
2.2 Assets and Damage Scenario Identification
In this section, I decided to combine the Steps 2 and 3 which are respectively Assets Identification and Damage Scenario Identification. In these 2 steps, if you still remember part 1, the goal is to identify all assets for which the compromission of one cybersecurity property can lead to a damage scenario. For the seek of simplicity the CIA triad is used exactly like in the standard. So, we will take here into account only the Confidentiality, Integrity and Availability properties. I invite you if you can to consider all properties from the CIANA Pentagon as homework 😉😉. You will see in below table the result all assets I identified with the properties and associated damage scenario.
For the first Asset data communication (brake command), the asset ID is A1, the cybersecurity properties that can be compromised are Integrity and Availability. As an example, I identified the damage scenarios when the Integrity property is compromised which resulted in :
DS1 : Vehicle fails to stop when the brake pedal is pressed, leading to a collision.
DS2 : Vehicle experiences unintended braking, causing abrupt stops and potential rear-end collisions.
DS1 and DS2 are of course the ID of the Damage scenarios.
| Asset ID | Assets | Cybersecurity Properties | Damage Scenario IDs | Cybersecurity Property which is Compromised | Damage Scenarios |
|---|---|---|---|---|---|
| A1 | Data communication (brake command) | Integrity (I), Availability (A) | DS1, DS2 | Integrity (I) | DS1: Vehicle fails to stop when the brake pedal is pressed, leading to a collision. DS2 : Vehicle experiences unintended braking, causing abrupt stops and potential rear-end collisions. |
| A2 | Brake Pedal Sensor | Integrity (I), Availability (A) | DS3, DS4 | Integrity (I) | DS3 : Incorrect sensor data leads to loss of braking control, causing a failure to stop. DS4 : Sensor malfunction causes unintended or inadequate braking response. |
| A3 | Firmware of BBW ECU | Confidentiality (C), Integrity (I) | DS5 | Integrity (I) | DS5 : Unauthorized modification of firmware causes loss of braking functionality. |
| A4 | Actuator Control Signals | Integrity (I), Availability (A) | DS6 | Integrity (I) | DS6 : Signals are altered, causing unbalanced braking across wheels, leading to loss of vehicle stability. |
| A5 | Communication Network (CAN bus) | Integrity (I), Availability (A) | DS7 | Integrity (I) | DS7 : Interference with CAN messages leads to delayed or incorrect brake responses. |
| A6 | Brake System Diagnostics Data | Confidentiality (C), Integrity (I) | DS8 | Integrity (I) | DS8: Diagnostic data alteration leads to undetected faults in the braking system, increasing the risk of failure. |
| A7 | Battery and Power Supply Control | Availability (A) | DS9 | Availability (A) | DS9: Loss of power results in total brake system failure, leading to a critical safety risk. |
| A8 | Software Update Mechanism | Confidentiality (C), Integrity (I) | DS10 | Integrity (I) | DS10: Unauthorized software updates introduce malicious code, compromising the BBW system’s functionality. |
| A9 | Diagnostic Services (Security Access) | Integrity (I), Availability (A) | DS11 | Integrity (I) | DS11: Bypassing security access allows unauthorized modification of system parameters. |
| A10 | Cryptographic Keys | Confidentiality (C), Integrity (I) | DS12 | Confidentiality (C) | DS12: Compromised keys allow decryption of sensitive data, leading to unauthorized access. |
| A11 | Debug Access | Confidentiality (C), Integrity (I) | DS13 | Confidentiality (C) | DS13: Unauthorized debug access exposes sensitive system information. |
| A12 | Calibration/Configuration Data Access | Integrity (I), Availability (A) | DS14 | Integrity (I) | DS14: Altered calibration data leads to improper system functioning. |
2.3 Threat Scenario Identification
In this section, we will focus on Step 4 of the TARA process: Threat Scenario Identification. The purpose of this step is to identify potential ways in which the cybersecurity properties of the identified assets can be compromised, leading to the realization of the associated damage scenarios. For this activity, I used the STRIDE methodology, which is one of the methods proposed by the standard. The threats are categorized into Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service (DoS), and Elevation of Privilege.
In the table below, you will find the identified threat scenarios, each corresponding to a specific damage scenario and the related cybersecurity property.
For example, for the asset data communication (brake command), the threat scenario identified is : Spoofing of CAN messages leads to loss of integrity of the brake command signals to the actuators, potentially causing the vehicle not to stop as expected. Therefore, this threat scenario directly impacts the Integrity property of the asset, which could lead to the damage scenarios DS1 and DS2 identified earlier.
| Damage Scenario | Threat Scenario ID | Threat Scenario |
|---|---|---|
| DS1: Vehicle fails to stop when the brake pedal is pressed, leading to a collision. | TS1 | Spoofing of CAN messages leads to loss of integrity of the brake command signals to the actuators, potentially causing the vehicle not to stop as expected. |
| TS2 | Tampering with brake command signals results in altered data, causing the vehicle not to stop as expected. | |
| DS2: Vehicle experiences unintended braking, causing abrupt stops and potential rear-end collisions. | TS3 | Tampering with brake command signals on the CAN bus results in unintended braking. |
| TS4 | Repudiation of unauthorized brake commands makes it difficult to trace the source of unintended braking. | |
| DS3: Incorrect sensor data leads to loss of braking control, causing a failure to stop. | TS5 | Spoofing of brake pedal sensor data results in incorrect information being sent to the BBW ECU, causing a failure to stop. |
| TS6 | Tampering with brake pedal sensor data leads to incorrect brake application, causing a failure to stop. | |
| DS4: Sensor malfunction causes unintended or inadequate braking response. | TS7 | Denial of Service (DoS) on the brake pedal sensor causes delayed or blocked data, resulting in inadequate braking response. |
| DS5: Unauthorized modification of firmware causes loss of braking functionality. | TS8 | Tampering with firmware leads to loss of braking functionality, compromising safety. |
| TS9 | Elevation of privilege is used to modify firmware and disable braking functions. | |
| DS6: Signals are altered, causing unbalanced braking across wheels, leading to loss of vehicle stability. | TS10 | Tampering with actuator control signals results in unbalanced braking across wheels, leading to loss of vehicle stability. |
| DS7: Interference with CAN messages leads to delayed or incorrect brake responses. | TS11 | Spoofing of CAN messages causes incorrect brake commands to be sent, resulting in delayed or incorrect brake responses. |
| TS12 | Denial of Service (DoS) attack delays or blocks brake commands, resulting in delayed or incorrect brake responses. | |
| DS8: Diagnostic data alteration leads to undetected faults in the braking system, increasing the risk of failure. | TS13 | Tampering with diagnostic data hides or alters faults, preventing proper maintenance and increasing the risk of failure. |
| DS9: Loss of power results in total brake system failure, leading to a critical safety risk. | TS14 | Denial of Service (DoS) or tampering with the power supply leads to a total loss of brake functionality, creating a critical safety risk. |
| DS10: Unauthorized software updates introduce malicious code, compromising the BBW system’s functionality. | TS15 | Elevation of privilege allows unauthorized software updates to be installed, introducing malicious code and compromising system functionality. |
| TS16 | Spoofing of the update server delivers unauthorized software updates, compromising system functionality. | |
| DS11: Bypassing security access allows unauthorized modification of system parameters. | TS17 | Elevation of privilege is used to bypass security access, allowing unauthorized modification of system parameters. |
| DS12: Compromised keys allow decryption of sensitive data, leading to unauthorized access. | TS18 | Spoofing identity using compromised keys to gain unauthorized access to secure communications. |
| TS19 | Tampering with cryptographic keys to bypass encryption and gain unauthorized access to sensitive data. | |
| DS13: Unauthorized debug access exposes sensitive system information. | TS20 | Tampering with debug interfaces grants unauthorized access to sensitive system data. |
| TS21 | Spoofing authentication mechanisms to gain access to debug interfaces, exposing sensitive system information. | |
| DS14: Altered calibration data leads to improper system functioning. | TS22 | Tampering with calibration data alters system parameters, leading to improper functioning and safety risks. |
2.5 Impact Rating of the Damage Scenario
In this section, we will focus on Step 5 of the TARA process namely the Impact Rating. The objective of this step is to evaluate the severity of the damage scenarios identified in the previous step, considering various impact categories such as Safety, Financial, Operational, and Privacy. By assigning an impact rating to each damage scenario, we can assess how critical the consequences would be if the attack is successfully performed.
The ISO/SAE 21434 standard provides guidance on how to rate these impacts, with the overall impact rating being categorized as Severe, Major, Moderate, or Negligible.
In the table below, we have assessed the impact of each damage scenario for each impact category. For instance, the impact rating for DS1 where the vehicle fails to stop when the brake pedal is pressed, leading to a collision is rated as Severe for Safety, Moderate for Financial, Major for Operational, and Negligible for Privacy with an overall impact rating of Severe.
If you don’t agree with my ratings, please, feel free to share yours in the comment section in order to provide another perspective for our networseclearning community! 🤲
| Damage Scenario ID | Damage Scenario | Safety Impact | Financial Impact | Operational Impact | Privacy Impact | Overall Impact Rating |
|---|---|---|---|---|---|---|
| DS1 | Vehicle fails to stop when the brake pedal is pressed, leading to a collision. | Severe | Moderate | Major | Negligible | Severe |
| DS2 | Vehicle experiences unintended braking, causing abrupt stops and potential rear-end collisions. | Severe | Moderate | Major | Negligible | Severe |
| DS3 | Incorrect sensor data leads to loss of braking control, causing a failure to stop. | Severe | Moderate | Major | Negligible | Severe |
| DS4 | Sensor malfunction causes unintended or inadequate braking response. | Severe | Moderate | Major | Negligible | Severe |
| DS5 | Unauthorized modification of firmware causes loss of braking functionality. | Severe | Moderate | Major | Negligible | Severe |
| DS6 | Signals are altered, causing unbalanced braking across wheels, leading to loss of vehicle stability. | Severe | Moderate | Major | Negligible | Severe |
| DS7 | Interference with CAN messages leads to delayed or incorrect brake responses. | Severe | Moderate | Major | Negligible | Severe |
| DS8 | Diagnostic data alteration leads to undetected faults in the braking system, increasing the risk of failure. | Major | Moderate | Major | Negligible | Major |
| DS9 | Loss of power results in total brake system failure, leading to a critical safety risk. | Severe | Moderate | Major | Negligible | Severe |
| DS10 | Unauthorized software updates introduce malicious code, compromising the BBW system’s functionality. | Major | Severe | Major | Negligible | Major |
| DS11 | Bypassing security access allows unauthorized modification of system parameters. | Major | Moderate | Major | Negligible | Major |
| DS12 | Compromised keys allow decryption of sensitive data, leading to unauthorized access. | Major | Severe | Major | Negligible | Major |
| DS13 | Unauthorized debug access exposes sensitive system information. | Moderate | Severe | Major | Negligible | Major |
| DS14 | Altered calibration data leads to improper system functioning. | Severe | Moderate | Major | Negligible | Severe |
2.6 Attack Path Analysis
In this section, we will focus on Step 6 of the TARA process which is the Attack Path Analysis. The goal of this step is to identify and analyze the different paths an attacker might take to exploit the vulnerabilities. Thanks to this, we can assess how an attacker could progress from the initial compromise to achieving their objectives, such as compromising the integrity of critical automotive systems.
In the table below, we analyze the attack paths for four selected threat scenarios namely TS1, TS5, TS14 and TS15 considering the different routes an attacker might take to achieve their goals. For example, in TS1, an attacker could exploit vulnerabilities in the telematics ECU via cellular network access, allowing him to send spoofed brake command signals through the gateway ECU to the BBW ECU which will lead to brake failure.
Don’t hesitate to propose your attack paths in the comments section! 🤲
| Threat Scenario ID | Threat Scenario | Attack Path |
|---|---|---|
| TS1 | Spoofing of CAN messages leads to loss of integrity of the brake command signals to the actuators, potentially causing the vehicle not to stop as expected. | 1. Attacker compromises the telematics ECU through cellular network vulnerabilities. 2. Compromised telematics ECU sends spoofed brake command signals to the gateway ECU. 3. Gateway ECU forwards the spoofed brake command signals to the BBW ECU. 4. BBW ECU relays the compromised signals to the actuators, causing brake failure. Alternative Attack Paths: • Physical Access: Attacker gains access via the OBD-II port. • Adjacent Access: Attacker uses Bluetooth interface to inject spoofed messages. |
| TS5 | Spoofing of brake pedal sensor data results in incorrect information being sent to the BBW ECU, causing a failure to stop. | 1. Attacker intercepts and manipulates signals from the wireless key fob. 2. Manipulated signal is used to spoof brake pedal sensor data. 3. BBW ECU receives and processes the incorrect data, leading to failure to stop the vehicle. Alternative Attack Paths: • Local Access: Attacker tampers with brake pedal sensors directly. |
| TS14 | Denial of Service (DoS) or tampering with the power supply leads to a total loss of brake functionality, creating a critical safety risk. | 1. Attacker compromises the vehicle’s power management system remotely. 2. Malicious commands disconnect or overload the power supply to the BBW system. 3. BBW system loses power, resulting in total brake system failure. Alternative Attack Paths: • Physical Tampering: Attacker disconnects or damages power supply cables. |
| TS15 | Elevation of privilege allows unauthorized software updates to be installed, introducing malicious code and compromising system functionality. | 1. Attacker identifies a vulnerability in the BBW ECU’s firmware update process. 2. Unauthorized software is uploaded via a compromised gateway ECU. 3. Malicious software alters the BBW ECU’s functionality, compromising braking control. Alternative Attack Paths: • Diagnostic Tool Exploit: Malicious software is injected via compromised diagnostic tool. |
2.7 Attack Feasibility Rating
In this section, we will address Step 7 of the TARA process namely the Attack Feasibility Rating. This step involves evaluating how feasible it is for an attacker to exploit the identified attack paths for each threat scenario.
The attack feasibility rating considers various factors such as the time needed to execute the attack, the expertise required, the knowledge of the system, the opportunity window available, and the equipment necessary. The ISO/SAE 21434 standard offers multiple approaches for this assessment, including the attack potential-based approach and the attack vector-based approach that we are going to use.
In the table below, we present the attack feasibility ratings for the selected threat scenarios TS1, TS5, TS14 and TS15 based on the complexity and likelihood of successfully executing the identified attack paths. For instance, in TS1, the high attack feasibility rating reflects the ease with which an attacker could exploit cellular network vulnerabilities to compromise the telematics ECU and cause brake failure.
- Rating using the Attack Vector-Based Approach
| Threat Scenario ID | Threat Scenario | Attack Path | Attack Feasibility Rating |
|---|---|---|---|
| TS1 | Spoofing of CAN messages leads to loss of integrity of the brake command signals to the actuators, potentially causing the vehicle not to stop as expected. | 1. Attacker compromises the telematics ECU through cellular network vulnerabilities. 2. Compromised telematics ECU sends spoofed brake command signals to the gateway ECU. 3. Gateway ECU forwards the spoofed brake command signals to the BBW ECU. 4. BBW ECU relays the compromised signals to the actuators, causing brake failure. | High |
| TS5 | Spoofing of brake pedal sensor data results in incorrect information being sent to the BBW ECU, causing a failure to stop. | 1. Attacker intercepts and manipulates signals from the wireless key fob. 2. Manipulated signal is used to spoof brake pedal sensor data. 3. BBW ECU receives and processes the incorrect data, leading to failure to stop the vehicle. | Medium |
| TS14 | Denial of Service (DoS) or tampering with the power supply leads to a total loss of brake functionality, creating a critical safety risk. | 1. Attacker compromises the vehicle’s power management system remotely. 2. Malicious commands disconnect or overload the power supply to the BBW system. 3. BBW system loses power, resulting in total brake system failure. | Low |
| TS15 | Elevation of privilege allows unauthorized software updates to be installed, introducing malicious code and compromising system functionality. | 1. Attacker identifies a vulnerability in the BBW ECU’s firmware update process. 2. Unauthorized software is uploaded via a compromised gateway ECU. 3. Malicious software alters the BBW ECU’s functionality, compromising braking control. | Medium |
- Rating using the Attack Potential-Based Approach
| Threat Scenario ID | Threat Scenario | Attack Path | ET | SE | KoIC | WoO | Eq | Value | Attack Feasibility Rating |
|---|---|---|---|---|---|---|---|---|---|
| TS1 | Spoofing of CAN messages leads to loss of integrity of the brake command signals to the actuators, causing brake failure. | 1. Attacker compromises the telematics ECU through cellular network vulnerabilities. 2. Spoofed signals are sent to the gateway ECU, then forwarded to the BBW ECU. 3. BBW ECU relays compromised signals to actuators. | 2 | 6 | 5 | 3 | 3 | 19 | Medium |
| TS5 | Spoofing of brake pedal sensor data leads to incorrect data being sent to the BBW ECU, causing a failure to stop. | 1. Attacker intercepts and manipulates signals from the wireless key fob. 2. Spoofed brake pedal data is sent to BBW ECU, leading to failure to stop the vehicle. | 2 | 6 | 4 | 2 | 2 | 16 | Medium |
| TS14 | DoS or tampering with power supply causes a total loss of brake functionality, creating a critical safety risk. | 1. Attacker compromises the vehicle’s power management system remotely. 2. Malicious commands disconnect or overload the power supply to the BBW system, resulting in total brake system failure. | 3 | 5 | 5 | 4 | 3 | 20 | Low |
| TS15 | Elevation of privilege allows unauthorized software updates, introducing malicious code and compromising functionality. | 1. Attacker identifies a firmware update vulnerability in the BBW ECU. 2. Unauthorized software is uploaded via a compromised gateway ECU, altering the BBW ECU’s functionality. | 3 | 6 | 5 | 3 | 3 | 20 | Low |
- ET: Elapsed Time
- SE: Specialist Expertise
- KoIC: Knowledge of the Item or Component
- WoO: Window of Opportunity
- Eq: Equipment
2.8 Risk Value Determination
In this section, we will address Step 8 of the TARA process which is the Risk Value Determination. This step involves calculating the overall risk value for each identified threat scenario by combining the impact rating with the attack feasibility rating.
The risk value is typically determined using a risk matrix that links the impact rating (ranging from Negligible to Severe) with the attack feasibility rating (ranging from Very Low to High). The resulting risk value ranges from 1 (minimal risk) to 5 (maximum risk).
The table below shows the risk value determination for the selected threat scenarios. We have used the attack feasibility rating obtained from the attack potential-based approach to ensure a more representative assessment.
- Here is the Risk Matrix Example we are going to use 😉
| Impact Rating \ Attack Feasibility Rating | Very Low | Low | Medium | High |
|---|---|---|---|---|
| Severe (S3) | 2 | 3 | 4 | 5 |
| Major (S2) | 1 | 2 | 3 | 4 |
| Moderate (S1) | 1 | 2 | 2 | 3 |
| Negligible (S0) | 1 | 1 | 1 | 1 |
This matrix can be used to determine the risk value by cross-referencing the impact rating with the attack feasibility rating as done in below table with our selected Threat Scenarios.
- Risk Value Determination for Selected Threat Scenarios
| Threat Scenario ID | Threat Scenario | Impact Rating | Attack Feasibility Rating | Risk Value |
|---|---|---|---|---|
| TS1 | Spoofing of CAN messages leads to loss of integrity of the brake command signals to the actuators, causing brake failure. | Severe (S3) | Medium | 4 |
| TS5 | Spoofing of brake pedal sensor data leads to incorrect data being sent to the BBW ECU, causing a failure to stop. | Severe (S3) | Medium | 4 |
| TS14 | DoS or tampering with power supply causes a total loss of brake functionality, creating a critical safety risk. | Severe (S3) | Low | 3 |
| TS15 | Elevation of privilege allows unauthorized software updates, introducing malicious code and compromising functionality. | Major (S2) | Low | 2 |
The risk value provides a clear indication of which threats require higher attention and which can be managed with lower-priority measures. This prioritization is crucial for effective cybersecurity risk management, as it ensures that resources are allocated to mitigate the most significant risks first.
In the next section, we will proceed to the final step of the TARA process, which involves determining the appropriate risk treatment decisions based on these risk values.
2.9 Risk Treatment Decision
In this section, we will address finally the last Step 9 of the TARA process which is of course Risk Treatment Decision, youpi!! 😀This step involves selecting the most appropriate risk treatment strategy for each identified threat scenario based on the determined risk values. The goal is to either eliminate the risk, reduce it to an acceptable level, share it with another party, or accept it if the risk is within acceptable limits.
The ISO/SAE 21434 standard outlines four primary risk treatment options:
- Avoiding the Risk : Eliminating the risk entirely by removing the risk source or discontinuing the activity that generates the risk.
- Reducing the Risk : Implementing measures to lower the risk to an acceptable level through controls or design changes.
- Sharing the Risk : Transferring the risk to another party, such as through contracts or insurance.
- Retaining the Risk : Accepting the risk as it is, often when mitigation is impractical or the cost of mitigation exceeds the benefit.
The table below outlines the risk treatment decisions for the selected threat scenarios :
| Threat Scenario ID | Threat Scenario | Risk Value | Risk Treatment Option |
|---|---|---|---|
| TS1 | Spoofing of CAN messages leads to loss of integrity of the brake command signals to the actuators, causing brake failure. | 4 | Reducing the risk |
| TS5 | Spoofing of brake pedal sensor data leads to incorrect data being sent to the BBW ECU, causing a failure to stop. | 4 | Reducing the risk |
| TS14 | DoS or tampering with power supply causes a total loss of brake functionality, creating a critical safety risk. | 3 | Reducing the risk |
| TS15 | Elevation of privilege allows unauthorized software updates, introducing malicious code and compromising functionality. | 2 | Reducing the risk |
Given the high and medium risk values associated with these threat scenarios, the recommended risk treatment strategy is to reduce the risk by implementing additional cybersecurity controls. These can include enhancing authentication mechanisms, improving system redundancy, or applying stricter access controls to prevent unauthorized actions.
CONCLUSION
Thank you for joining me on this journey through the Threat Analysis and Risk Assessment (TARA) process as applied to the Brake By Wire (BBW) system. I hope you found this practical tutorial informative. I hope by now, you have a solid understanding of how to identify assets, assess threats, evaluate risks, and determine the appropriate risk treatment strategies to protect critical automotive systems. 🤲
Remember, cybersecurity in the automotive industry is about ensuring the safety, security, and trust of everyone who gets behind the wheel. As vehicles become more connected, the importance of robust cybersecurity measures will only continue to grow. 😊
If you found this tutorial helpful, feel free to share it with others who might benefit from it. And if you have any questions, suggestions, or just want to share your thoughts, don’t hesitate to leave a comment. Let’s keep the conversation going and continue learning together within our community of networkseclearners! 😊
Until next time, stay curious and keep exploring the world of automotive cybersecurity! 🚗🔒
References :
1. ISO/SAE 21434:2021 – Road Vehicles Cybersecurity Engineering. This standard outlines the framework for managing cybersecurity risks in the automotive industry, including the TARA process.
2. UNECE WP.29 – World Forum for Harmonization of Vehicle Regulations. This regulation includes cybersecurity requirements under Regulation No. 155, focusing on vehicle type approvals concerning cybersecurity.
3. Brake-by-Wire Systems: Benefits and Challenges – An overview of Brake-by-Wire technology. Available at https://cecas.clemson.edu/cvel/auto/AuE835_Projects_2011/Ramesh_project.html
4. STRIDE Threat Model – Developed by Microsoft, this framework is widely used in threat scenario identification, particularly in the context of cybersecurity for automotive systems.

You’ve crafted something truly timeless here — writing that will continue to resonate with readers for years to come.
I do not even understand how I stopped up here, but I thought this submit was
good. I do not recognise who you are but certainly you’re going to a well-known blogger
if you happen to are not already. Cheers!